Information security: A 20-year retrospective
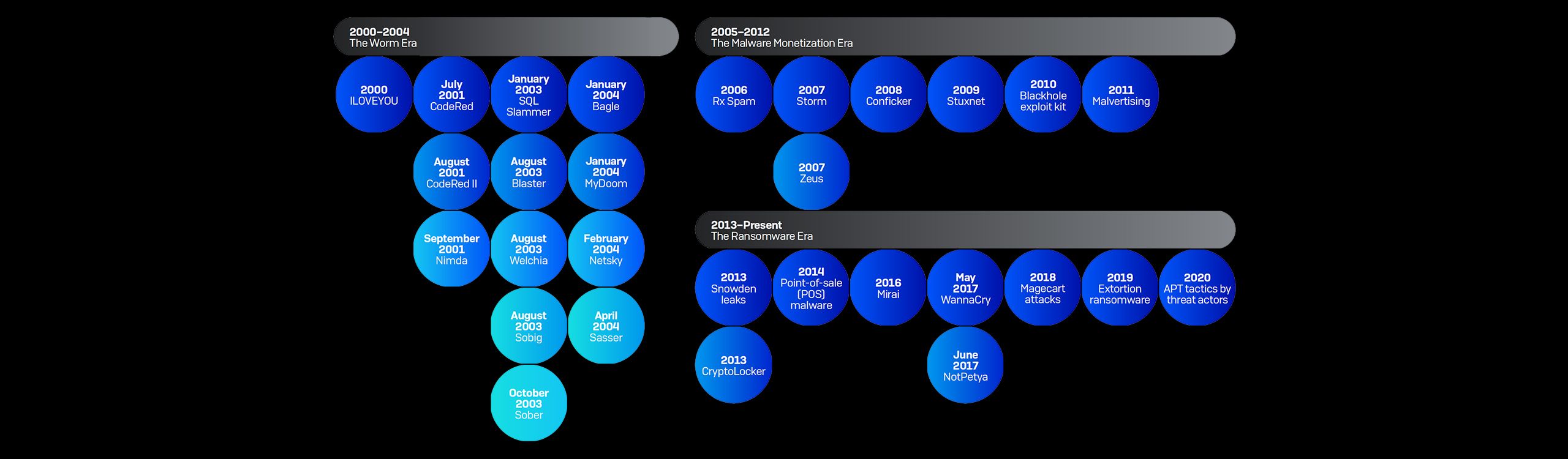

The turn of the millennium marked a milestone, when information security became a professional discipline and a bona fide industry. This timeline of threats and events represent significant, representative moments in the evolution of threat behavior.
As both enterprises and individuals adopted the internet for both business and entertainment, large networks were ripe targets for the emergence of prolific worms – self-propagating malware. Cumulatively, worms infected tens of millions of systems worldwide and cost over $100 billion in damages and remediation costs.
2000–2004 - The Worm era
2000 - ILOVEYOU
The ILOVEYOU worm used a social engineering trick that persists even today: It arrived as a spam email attachment, eventually infecting about 10% of all internet-connected Windows computers.
July 2001 - CodeRed
Named after the flavor of Mountain Dew its discoverers were drinking at the time, CodeRed used a buffer overflow vulnerability in IIS to spread itself and deface websites. It was followed a month later by an upgraded version that installed a backdoor on networked computers.
August 2001 - CodeRed II
September 2001 - Nimda
January 2003 - SQL Slammer
At only 376 bytes, Slammer exploited a buffer overflow in Microsoft database applications. Doubling its infections every 8.5 seconds, Slammer took down large swaths of the internet in only 15 minutes.
August 2003 - Blaster
Blaster was created by reverse engineering a Microsoft patch a couple months ahead of the first Patch Tuesday. It exploited a buffer overflow vulnerability in the RPC service of Windows XP and 2000 systems and launched a DDoS attack against windowsupdate.com if the day of the month was greater than 15, or the month was September or later.
August 2003 - Welchia
August 2003 - Sobig
October 2003 - Sober
January 2004 - Bagle
January 2004 - MyDoom
It is estimated that 25% of all emails sent in 2004 originated with the MyDoom worm, which prolifically emailed itself to new victims and engaged in a denial-of-service (DDoS) attack.
February 2004 - Netsky
April 2004 - Sasser
2005-2012 - The Malware Monetization era
Until around 2005, malware incidents could be chalked up to curiosity or disruption. Botnet malware, designed for stealth and profit, dominated. This era also saw the start of so-called pharmacy spam. Exploits against software vulnerabilities became key components of malware, which enabled malvertising. Wherever there was the potential for financial gain, cybercriminals exploited those opportunities.

2006 – Rx Spam
What had been a mere annoyance (or a way to propagate worms), became a lucrative business selling mostly counterfeit prescription medicines advertised through spam. It's estimated that pharma spammers made billions of dollars selling medicines most people could get just by going to their doctors.
2007 - Storm
2007 - Zeus
2008 - Conficker
Conficker rapidly infected millions of computers worldwide but did not result in much damage. We still don't know the worm's true purpose, but thousands of hosts remain infected to this day, and Conficker scan traffic routinely is detected as part of the internet's "background radiation."
2009 - Stuxnet
Stuxnet was one of the first digital weapons to target a physical system: Nuclear refinement centrifuges used by Iran to enrich uranium. Stuxnet's enduring legacy is that it permanently opened the door to nation-states' use of malware as a tool of war.
2010 - Blackhole exploit kit
Exploit kits – toolkits targeting software vulnerabilities – bound different parts of the cybercrime ecosystem together. Crimeware- as-a-Service was born when the creators of the Blackhole Exploit Kit began offering their services.
2011 - Malvertising
People's computers are not getting more secure. They're getting more infected with viruses. They're getting more under the control of malware.
2013–Present - The Ransomware era
Ransomware has had the most profound impact on this era. While worms, banking trojans, malvertising and spam persist, nothing has come close to rivaling ransomware's destructive force. Damage estimates from ransomware attacks over the past seven years are in the trillions of dollars. Ransomware is also most likely the first form of malware linked to a human death. Moreover, many of today's threats ultimately deliver ransomware and, like exploit kits, it has provided a nitro-fueled boost to an already thriving cybercrime ecosystem.

2013 - Snowden leaks
2013 - CryptoLocker
During its short existence, CryptoLocker provided future criminals with a winning formula by mating two existing technologies: encryption and cryptocurrencies. The threat landscape was forever changed by CryptoLocker and its aftershocks are still being felt today. Three months after launch, the bitcoin wallet used by CryptoLocker contained nearly $30 million.
2014 - Point-of-sale (POS) malware
2016 - Mirai
May 2017 - WannaCry
WannaCry, the most widespread ransomware-worm hybrid seen, demonstrated (again) how a lapse in patching can have dire consequences. It relied on exploits stolen from the NSA and publicly released by The Shadow Brokers. The attacks forced Microsoft to release out-of-band updates for unsupported products.
June 2017 - NotPetya
NotPetya crippled some of the world's largest shipping and logistics companies, reportedly causing over $10 billion in damages. Some of the affected companies have yet to fully recover.
2018 - Magecart attacks
2019 - Extortion ransomware
In an attack against the city of Johannesburg, South Africa, the criminals behind Maze ransomware pioneered the use of extortion. They not only encrypted and stole data, but also threatened to publish the stolen data if companies didn't pay. This tactic has been copied by many other ransomware crews as a hedge against the targets having good backups.
2020 - APT tactics by threat actors
The adoption of nation-state tools and tactics, which began in the past couple of years, went mainstream in 2020. Professional cybercrime gangs use sophisticated tools like Cobalt Strike to devastating effect, while some groups (Dharma) are baking it into point and shoot toolkits for novices to use.
I think computer viruses should count as life, I think it says something about human nature that the only form of life we have created so far is purely destructive. We've created life in our own image.